Original Source – SAML SSO with Shibboleth
Author Archives: gluuservers10
Gluu Server for Educational Institutions
As cloud-based services continue to gain importance and adoption, many campuses are still struggling to offer integration strategies that work well with modern IT architectures, systems, and services.
The Gluu Server enables an institution to support open web protocols for single sign-on and access management, and the annual subscription equips an institution with the support it needs to offer a secure access management service day after day.
100% Open Source Software
With a Gluu Server, your institution is never subject to predatory licenses or per user fees. All components of the Gluu Server are free to use in production. Each component of the Gluu Server fulfills a different requirement:
- Shibboleth is one of the most dependable open source SAML single sign-on servers available and is in production at more than 5,000 organization’s worldwide.
- Asimba SAML Proxy enables an organization to consolidate inbound SAML authentication from the IDPs of partners to a website or app. Support for Asimba is not included with the Gluu Server EDU subscription, but can be provided as an additional option.
- oxAuth is Gluu’s inter-op leading OpenID Connect IDP and industry leading UMA Authorization Server (AS).
- Gluu OpenDJ LDAP is our compiled and supported version of OpenDJ. LDAP provides persistence for the Gluu Server, and can be used as the authoritative source of identity if needed.
- oxTrust is the server administration application. In oxTrust, the server admin can manage and configure SAML & OpenID Connect single sign-on, and script policies to enforce custom authentication workflows and control access to web resources like folders and API’s.
Your Infrastructure. Your Security Policies.
All Gluu Servers are self-hosted. Gluu, as an organization, never stores or hosts your personally identifiable information (PII). With a Gluu Server, you can:
Leverage an existing authentication system such as Active Directory.
Call external security API’s such as two factor authentication mechanisms or intrusion detection software.
Enforce access management, and multi-step, multi-factor authentication based on attributes and/or groups.
Gluu EDU Build / Operate Subscription
An instance of the Gluu Server is deployed in your data center on your VM’s. Both your organization and Gluu maintain root access to the servers.
Starts at $30,000 (up to two servers)
EDU Support
No per user or per connection fees
24/7 monitoring and reporting
Gluu releases first version of Open ID connect (OX)
Gluu announced the release of open ID connect (OX) version 0.0, an implementation of the XDI 1.0 standard under review by the OASIS XDI Technical Committee. This initial release provides a core Java API for XDI, a graphical browser for displaying XDI graphs, and an XDI server which provides XDI persistence, operations, and messaging. OX leverages XRI 3.0, a separate OASIS proposed standard for persistent and re-assignable naming objects on the Internet.
“The imminent completion of the XDI 1.0 standard represents the culmination of years of hard work by the OASIS XDI Technical Committee. All of us at Gluu are grateful for the opportunity to bring this vision to life in code,” said Michael Schwartz, Founder / CEO of Gluu. “Today, privacy on the Internet is broken. The architects of the Internet did not design the network to address the complex security and privacy requirements that are needed by our society. OpenID connect single sign on and XDI technology is a deep structural solution to empower people and organizations to both share and protect data that is essential for their digital existence,” he continued.
About Gluu:
Gluu publishes free open source Internet security software that universities, government agencies and companies can use to enable Web and mobile applications to securely identify a person, and manage what information they are allowed to access. Using a Gluu Server, organizations can centralize their authentication and authorization service and leverage standards such as OpenID Connect, UMA, and SAML 2.0 to enable Single sign on server (SSO) and trust elevation.
How does SAML work? IdP’s & SP’s
SAML, or Security Assertion Markup Language, is the leading SSO protocol today and is a valuable standard to understand in order to fully comprehend how SAML active directory single sign on works.
SAML boils down to attribute exchange through the creation of trust relationships between IdP’s and SP’s. A basic example is signing into your active directory to log on to your work computer in the morning, and automatically gaining access to your company gmail or salesforce.
The three main components of the SAML protocol:
Assertions – Most common are the following 2 SAML assertions:
Authentication assertions are used to make people prove their identities.
Attribute assertions are used to generate specific information about the person, for example their phone number or email address.
Protocol – This defines the way that SAML asks for and gets assertions, for example, using SOAP over HTTP.
Binding – This details exactly how SAML message exchanges are mapped into SOAP exchanges.
5 Benefits of using a SAML IdP:
There are many reasons to use a SAML IdP. Besides being the dominant single sign on protocol in use today, there are a host of reasons an organization should consider implementing a SAML IdP. Here are 5 reasons to use SAML for SSO:
1. User passwords never cross the firewall, since user authentication occurs inside of the firewall and multiple Web application passwords are no longer required.
2. Web applications with no passwords are virtually impossible to hack, as the user must authenticate against an enterprise-class IdM first, which can include strong authentication mechanisms.
3. “SP-initiated” two factor security provides access to Web apps for users outside of the firewall. If an outside user requests access to a Web application, the SP can automatically redirect the user to an authentication portal located at the Identity Provider. After authenticating, the user is granted access to the application, while their login and password remains locked safely inside the firewall.
4. Centralized federation provides a single point of Web application access, control and auditing, which has security, risk and compliance benefits.
5. A properly executed identity federation layer that satisfies all of the use cases described above and supports multiple protocols can provide an enterprise-wide, architecturally sound Internet SSO solution.
Gluu’s Business Model
After listening to a session at SXSWV2V by Patrick van der Pijl, I was encouraged to read Business Model Generation, and to develop the business model diagram below for Gluu.
Gluu is an Austin, TX start up that provides open source and on demand cloud identity and trust management. Gluu leverages standards such as OpenID Connect, SAML 2.0, and SCIM to make achieving single sign-on (SSO) secure and easy. Deployed quickly on public and private cloud servers, Gluu’s cloud identity platform helps organizations addresses the installation and operational issues of an organizational identity provider at a predictable annual cost.
Gluu’s OpenID Connect platform to support multi-party federations
Gluu, a leading open source cloud identity provider saml, today unveiled its plan for multi-party federations based on OpenID Connect. Details of the proposed design have been published on the OpenID Wiki. This move reflects Gluu’s developmental roadmap for OpenID Connect, and is also a call to the OpenID developer community en masse for support on this important project.
“Currently, multi-party federations are only achievable via the SAML protocol,“ said Gluu CEO Michael Schwartz. “By designing multi-party federations in OpenID Connect, we are hoping to make it easier for organizations, websites, and applications to provide a simpler cloud identity experience to business people, developers and end users. We need both tools and rules to enable privacy and security on the internet, and this proposed enhancement to the OpenID Connect standard will be an important tool for the Internet community.”
InCommon is a good example of SAML multi-party federations in the higher education sector. When a University joins InCommon, they agree to operating policies, procedures, and schema that allows them to establish single sign-on with resource providers that have also agreed to certain level of privacy and trust. This simplifies the process of establishing trust with multiple entities by eliminating the need to structure individual SSO agreements one by one.
Gluu’s goal is to make managing trust with clients easier for organizations, and publishing numerous active directory single sign on endpoints easier for resource providers. Much of the conceptualization and design for this has been completed, and Gluu expects to implement active directory single sign on in its open source OpenID Connect platform, OX, by the end of 2012.
About Gluu:
Gluu is an Austin, TX start up that provides open source and on demand cloud identity and trust management. Gluu leverages standards such as OpenID Connect, SAML 2.0, and SCIM to make achieving single sign-on (SSO) secure and easy. Deployed quickly on public and private cloud servers, Gluu’s cloud identity platform helps organizations addresses the installation and operational issues of an organizational identity provider at a predictable annual cost.
17 Recommended Requirements for an Identity and Access Management POC
 We get requests for POC’s quite often. In an attempt to provide tactical guidance to organizations developing an identity and access management POC, the following are our top recommended criteria for evaluation.
We get requests for POC’s quite often. In an attempt to provide tactical guidance to organizations developing an identity and access management POC, the following are our top recommended criteria for evaluation.
By adding some or all of these requirements to your POC, your organization can limit vendor lock-in and ensure that the solutions considered will satisfy both current and future identity and access management challenges.
1.Published results for OpenID Connect Provider (OP) and Relying Party (RP) software in InterOp 5 that indicate the vendor has at least 80% coverage of both the RP and OP defined inter-op use cases. For example, here are Gluu’s InterOp results.
2.Support for UMA 0.9 Authorization Server endpoints, Resource Server endpoints, and supported client code. Include details on how the policy mapping is made to UMA scopes.
3.Support for adaptive authentication: i.e. the ability to make changes to the business logic of authentication at run time. Or how to use a 1 or 2 step authentication workflow depending on the person (i.e. the IT group has to use two-factor authentication, normal users can use passwords…)
4.Support for the publication of SAML Multi-party federation management, including a workflow tool for vetting SAML IDPs and SPs to join the federation, and other federation administrator operational tools.
5.Support for public user registration.
6.Support for invitation code based user registration.
7.IDP must be able to specify authentication type on a per SP basis. For example, use passwords for Google, but tokens for Salesforce.
8.Support for SAML persistent non-correlatable identifiers.
9.Support for per SP attribute release policies in SAML.
10.Native mobile client application for strong authentication, along with mobile device enrollment and management features.
11.Support for the SCIM user management API’s to enable your organization to interface with the IDM system to send updates about users.
12.Supported SAML client API for Java.
13.Supported OpenID Connect client API for Java.
14.Supported UMA client API for Java.
15.Supported SCIM Client code.
16.Support for open standards based API access control using headless API’s and a mobile client (i.e. no browser).
17.Free open source license for binaries for major linux operating systems so your organization can easily take over operation and provide a reasonable free open source option to partners who do not want to purchase expensive enterprise software.
OpenID Connect and UMA Apache HTTPD Plugins Are On the Way!
The Gluu Management was upbeat and thanked all the supporters of their CrowdTilt Campaign $7,975 that had been crowd-funded to enable the development of Open Source OAuth2 plugins for the Apache HTTPD server!
Support that flowed in from various sources and quarters has been given due credit by the management of Gluu
1) Andrew Hughs for convincing me, despite my original skepticism, that we should try to crowd fund the plugin. Not only did we raise $8,075, we generated a lot of awareness, and built the community of OX supporters in the process. Andrew was a key catalyst in making this happen!
2) Eve Maler (and the UMA team) for writing UMA. OX’s vision for open source access management for organizations would not be possible without UMA. For Eve and her UMA collaborators, it has been a marathon effort for many years, and its a miracle that people would be as committed to the effort! Thank you for your hard work which makes something like a plugin even possible!
3) Kantara One of the key catalysts in this campaign, we should all thank Joni Brennan for her work on UMA and other important standards efforts. A neutral partner to help the participants of the ecosystem is essential.
4) OpenID Connect Working Group: For also being so damn persistent… few people realize how many issues need to be resolved to get a large and important standard written. Without their work, we would have nothing to implement.
5) 30+ passionate identity evangelists. Individuals were the first contributors to the campaign, and funded 30%, which is a key sign of support. Without this, I don’t think the corporate sponsors would have joined. This group did double what I expected… and many people even upped their contribution when it looked like we were not going to make it! Thank you everyone!
6) CrowdTilt I have been a fan of CrowdTilt since it launched a few years back. Behind the scenes, they are making sure it all works. Thank you all for your dedication!
7) Falcon Systems Consulting of Japan. Falcon was the first and largest corporate sponsor. I was short $5,000 on our campaign. By offering to cover half, it made the raising the final third seem possible. After closing the loop with potential corporate sponsors, we tilted! I went into work not thinking the campaign had failed, and I left work, we had commitments to get the campaign tilted. Thank you to Masamichi Takahashi for supporting open source and open standards and leading the way in Japan!
8) Symas. Thank you to Marty Heyman and Shawn McKinney for contributing to the campaign, for their hard work developing an open source identity stack, and for inviting me to the Java One IAM Panel
9) ForgeRock. We’re really happy to collaborate with ForgeRock. Without other implementers of OpenID Connect and UMA, Gluu’s platform would be just as proprietary as the monolithic IAM solutions. ForgeRock’s financial support is really appreciated, but their future participation in open standard interops will pay even bigger dividends for the Internet. Special thank you to Lasse Andresen and Allen Foster!
10) All you guys Thank you for to everyone else out there who helped us by RE-TWEETing and helping to get the word out. We had more than 3000 twitter clicks on our campaign. Without your help, we couldn’t have found all the poeple out there who want

OpenID Connect and UMA Apache HTTPD Plugins Are On the Way!
The Gluu Management was upbeat and thanked all the supporters of their CrowdTilt Campaign $7,975 that had been crowd-funded to enable the development of Open Source OAuth2 plugins for the Apache HTTPD server!
Support that flowed in from various sources and quarters has been given due credit by the management of Gluu
1) Andrew Hughs for convincing me, despite my original skepticism, that we should try to crowd fund the plugin. Not only did we raise $8,075, we generated a lot of awareness, and built the community of OX supporters in the process. Andrew was a key catalyst in making this happen!
2) Eve Maler (and the UMA team) for writing UMA. OX’s vision for open source access management for organizations would not be possible without UMA. For Eve and her UMA collaborators, it has been a marathon effort for many years, and its a miracle that people would be as committed to the effort! Thank you for your hard work which makes something like a plugin even possible!
3) Kantara One of the key catalysts in this campaign, we should all thank Joni Brennan for her work on UMA and other important standards efforts. A neutral partner to help the participants of the ecosystem is essential.
4) OpenID Connect Working Group: For also being so damn persistent… few people realize how many issues need to be resolved to get a large and important standard written. Without their work, we would have nothing to implement.
5) 30+ passionate identity evangelists. Individuals were the first contributors to the campaign, and funded 30%, which is a key sign of support. Without this, I don’t think the corporate sponsors would have joined. This group did double what I expected… and many people even upped their contribution when it looked like we were not going to make it! Thank you everyone!
6) CrowdTilt I have been a fan of CrowdTilt since it launched a few years back. Behind the scenes, they are making sure it all works. Thank you all for your dedication!
7) Falcon Systems Consulting of Japan. Falcon was the first and largest corporate sponsor. I was short $5,000 on our campaign. By offering to cover half, it made the raising the final third seem possible. After closing the loop with potential corporate sponsors, we tilted! I went into work not thinking the campaign had failed, and I left work, we had commitments to get the campaign tilted. Thank you to Masamichi Takahashi for supporting open source and open standards and leading the way in Japan!
8) Symas. Thank you to Marty Heyman and Shawn McKinney for contributing to the campaign, for their hard work developing an open source identity stack, and for inviting me to the Java One IAM Panel
9) ForgeRock. We’re really happy to collaborate with ForgeRock. Without other implementers of OpenID Connect and UMA, Gluu’s platform would be just as proprietary as the monolithic IAM solutions. ForgeRock’s financial support is really appreciated, but their future participation in open standard interops will pay even bigger dividends for the Internet. Special thank you to Lasse Andresen and Allen Foster!
10) All you guys Thank you for to everyone else out there who helped us by RE-TWEETing and helping to get the word out. We had more than 3000 twitter clicks on our campaign. Without your help, we couldn’t have found all the poeple out there who want
Cable operator Charter (S CHTR) is looking to bring the cloud to its customers’ cable boxes, regardless of when those devices were made: Charter CEO Tom Rutledge said during the company’s earnings call Thursday that his company intends to roll out a new, cloud-based UI to all of its set-top boxes next year. Rutledge added that initial tests in Fort Worth, Texas have been promising, and that Charter will expand these tests to additional markets later this year. Charter announced 29,000 video subscriber losses Thursday, down from 55,000 a year ago.
Charter is using cloud virtualization technology from ActiveVideo to revamp the user interfaces of its cable boxes without actually having to upgrade the hardware. This is being accomplished by hosting the UI in the cloud, where it is rendered into a video stream that can be played back even with legacy pay TV hardware. The…
View original post 274 more words
School Ring Federation
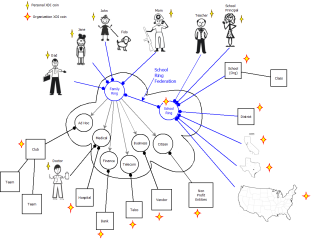 At a high level, this blog is about how xdiCoin and OX messaging could be used to support OpenID Connect 1.0 multi-party federations.
At a high level, this blog is about how xdiCoin and OX messaging could be used to support OpenID Connect 1.0 multi-party federations.
The interactions between individuals and organizations has become increasingly complex. By using OX, people or organizations can create data federations. Federations will enable simplification of trust by standardizing the vocabulary, policies and operating procedures for the respective data sharing relationship.
While talking with Denise Tayloe from Privo last week, I realized there is a chicken and the egg problem with identifiers. As soon as kids have a coin, I realized that the most important trust ring to draw is your Family Ring.
The Family Rings solves two problems I’ve been thinking about recently (1) how do my children interact with companies (Lego, Moshi Monsters, etc) (2) how do my kids interact with the school. In order to manage these relationships, the organizations in question need to understand that I am the parent.
The School Ring is my idea to show the potential opportunities for federation. oxPlus is a private social networking application for a K-12 school that we wrote as part of the project with ID3. We are planning to re-launch oxPlus on a new public website. We will re-brand it, and enable open registration (which will help for the web access management system wam).
With open registration, people can obtain OpenID Connect 1.0 credentials and an OX personal datastore. OX is used to store the parent child relationships. oxPlus also provides tools to create a school in OX. Even a homeschooling parent could register their own school, specify that they are the teacher, and point to their kids as the students.
This type of standardization enables kids to receive services (with their parents consent), and for schools to make data available “up the stream,” within the confines of the rules of the federation. This is how governments can get real time test scores and access to richer content. Improved inter-operability would also help students who move to a new district or state, giving the receiving educators a better understanding of a students capabilities on an apples:apples basis.